NOTICE: We’ve created an archive of all major developments related to the Pocophone F1 smartphone. We are continuously updating that page with latest Poco F1 news so that you don’t need to search for information related to the device on a daily basis. Head here to access that page.
If you love to tinker with your phone with third party kernels and custom roms, Poco F1 should be godsend for you. Xiaomi is pretty much consistent with the release of kernel source, and Android 10 is also available for the phone via stable channel.

It’s not just the official updates that made the phone famous. Similar to the first OnePlus phone, Pocophone F1 has a vast aftermarket development community. You can find leading custom Android distributions for this device. In fact, some developers bought Poco F1 just for the sake of supporting it.
Park Ju Hyung, who is better known as ‘arter97‘ in the fraternity, does provide custom kernel for this device. The development of arter97 kernel for Poco F1 has recently been shifted from the XDA thread. Well, a serious consequence now comes into existence.
I already see couple of people reporting that they bricked their device from the “leak” Telegram group.
I assume many more accounting that some won’t have a secondary device to use Telegram.I don’t know what to say to those using the leaked kernel other than that you played yourself.
While I never anticipated that this would actually happen, I did post a warning.-arter97
As you can see, someone decided to exploit the fame of the arter97 kernel and started distributing a modified copy of it. Not only publishing the internal test builds to the public is a disrespectful act, but bricking the phones is also a serious offence!
Due to the rapidly increasing number of brick reports, the developer has issued a notice to identify the tampered copy of his kernel packages.
The versioning string is different. My release tells you which exact Git HEAD commit was at the time of building. The “r20b6+” means that it’s been built without CONFIG_LOCALVERSION_AUTO set.
Also, my build server’s host name is “arter97-dgist”. The leaked one is “arter97_dgist”.
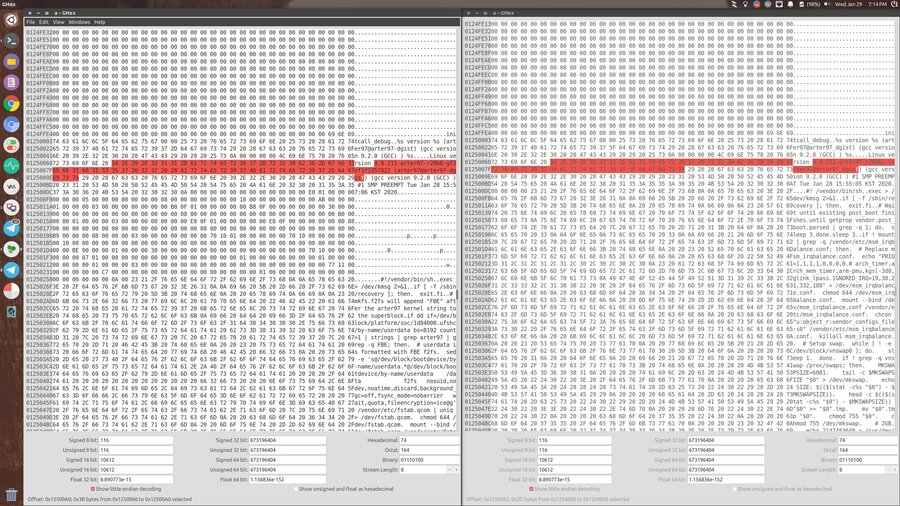
The actual reason behind the bricking is rather interesting. The impersonator has modified the binary to wipe out the UFS and bootloader partition. While it is possible to resurrect your Poco F1 after this mishap, the process is not very straightforward.
The “leaker” actually wanted to brick devices. They injected a piece of code to execprog to wipe all internal UFS storage(including the bootloader) on January 29th 00:00 UTC time.
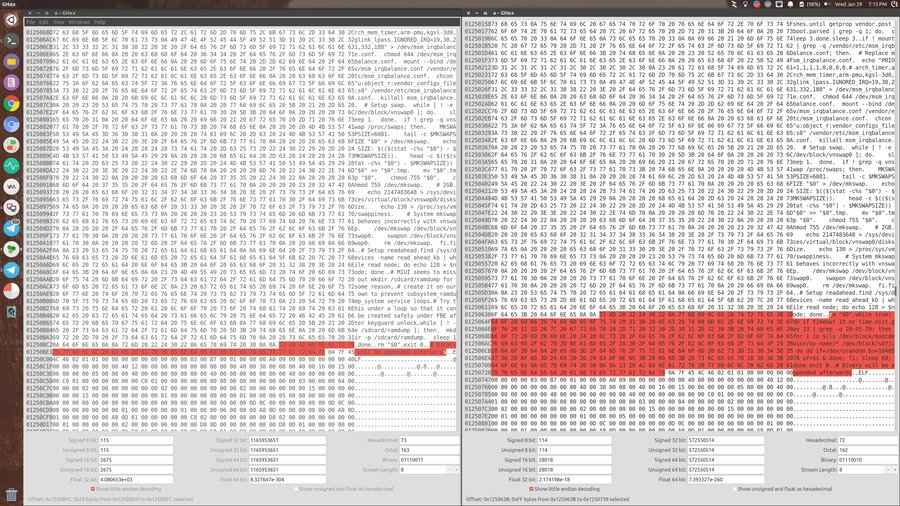
At this moment, it is advisable to keep distance from kernel packages from unverified sources to keep your Pocophone F1 safe. If you want to try out arter97 kernel, please follow the dev’s official Twitter handle for status updates.
PiunikaWeb started as purely an investigative tech journalism website with main focus on ‘breaking’ or ‘exclusive’ news. In no time, our stories got picked up by the likes of Forbes, Foxnews, Gizmodo, TechCrunch, Engadget, The Verge, Macrumors, and many others. Want to know more about us? Head here.