Inspired by @Scott_Helme, I got onboard @The_Pi_Hole bandwagon today. This is so awesome - blocking crappy stuff on the network automatically without the risk of installing browser extensions: https://t.co/yErsIWRDhW
— Troy Hunt (@troyhunt) September 26, 2018
Revenue generation via ads is nothing new. After the smartphone boom, the digital ad industry reached to a new height. Phone OEMs are bundling ads in the core of the operating system itself so that typical users have to consume them.
Advertising has been and will continue to be an integral part of Xiaomi’s Internet services, a key component of the company’s business model. At the same time, we will uphold user experience by offering options to turn off the ads and by constantly improving our approach towards advertising, including adjusting where and when ads appear. Our philosophy is that ads should be unobtrusive, and users always have the option of receiving fewer recommendations.
(Source)
In-app ads are also very common. From indie developers to gigantic publishers – everybody is taking part in this practice, no matter how much intrusive the ads are.
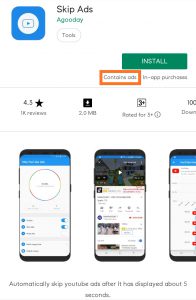
Power users can opt for adblockers, block the ad domains via editing ‘hosts’ or even modify the firmware of the router to stop the ads altogether. However, these options are not suitable for everyone.
PSA: Please take a look at the Pi-hole project.
Yesterday a friend of mine asked for my help regarding an uncanny situation. She was getting random browser pop ups in her phone which were redirected to novelcamp.net or appsquare.net.
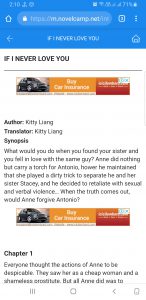
At first, it seemed to be another trivial adware attack; probably a random app with tons of dubious permissions was causing it.
Well, I was wrong. She did a factory reset before asking me, and such pop ups were happening even without any third party apps.
“It’s a Samsung phone.”, she said. With these parameters in hand, I decided to dig deeper.
Guess what? She is part of a bigger clan of victims.
@Bitdefender any news on the novelcamp and appsquare adware recently plaguing android devices being found and removed yet? :((
— Ambassador Janice🍁 (@NH_Janice) February 21, 2019
なんか最近googleplayからアプリのインストールとかアップデートとかすると海外の小説サイト(novelcamp)とか海外のアプリ紹介ページ(appsquare)とかに飛ばされるんだけどウイルスか……?その割には飛ばす先が真っ当なサイトの気がするんだが。。
— 高科鮭 (@takashina_his) February 22, 2019
There are several similar reports, scattered across various subreddits.
This thread is the most elaborate and longest one among them. The thread creator looks well-informed, as he provided extensive details of the scenario.
From the feedback, I notice the following patterns:
- Samsung phones are majorly affected.
- In some cases, the Videoder app is installed.
- Resetting cookies or site data, reinstalling Chrome, even factory resetting the phone can not help.
- Antimalware/antivirus products can not detect anything conclusive.
Our analysis
It turns out that appsquare.net and novelcamp.net are related to each other, as the former has a link to the latter inside the hamburger button. In both cases, the site layouts are not ‘actually’ responsive, rather they are modified to imitate native apps.
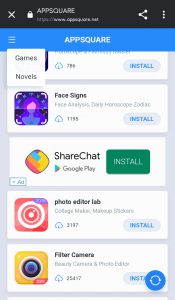
The links are heavily entangled with multiple advertising and analytics platforms, such as AppsFlyer and Batmobi.
https://app.appsflyer.com/com.ticno.olymptrade?pid=batcloud_int&c=CPA_IN&af_sub1=cpa_rk_batmobi_IN_android&af_sub2=CPA&af_siteid=20362338&af_click_lookback=1d&clickid=AAAAAEuFE91FFw8Dv1F4vD47078w554799E36_EDi_20190223200658_EDi_48230666_EDi_1004025_EDi__EDi__EDi__EDi_103.192.168.2_EDi_TI_EDi_977E827D4E827962_EDi_505_EDi_4w59uF5970E443vwE286v10E67D201w7_EDi_0_EDi__EDi__EDi_0_EDi_0_EDi__EDi_569D22E4-Eu66-4671-Dv79-Dv1D53393FuD_EDi_15419_EDi_0&android_id=&advertising_id=4f59dc5970b443efb286e10b67a201f7&idfa=4f59dc5970b443efb286e10b67a201f7#reqid#&utm_medium=cpa&utm_term=20362338&is_retargeting=false&af_reengagement_window=30d
A quick look inside the pages reveals frequent usage of Batmobi APIs.
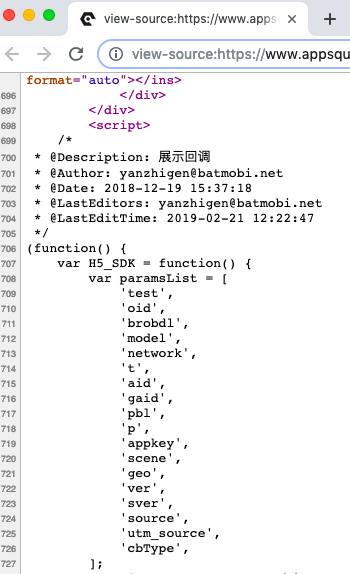
The name rings a bell! Remember the digital ad monkey business, busted by Kochava and BuzzFeed News last year? Cheetah Mobile and Kika Tech were accused of committing ad fraud in several most downloaded apps, including Clean Master and Battery Doctor.
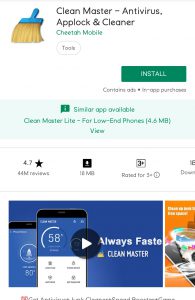
Google promptly took steps: they banned two of those apps from Play Store and blacklisted three ad network SDKs due to app install attribution abuse.
Cheetah Mobile published two formal press releases after the drama. According to them, they collaborate with various SDK providers and have “no control over these third party advertising platforms”.
The Company has neither the intention or ability to direct such advertising platforms to engage in the alleged “click injections.” In addition, given the overwhelming contribution of revenues from third party adverting platforms, the Company has no intention to engage in any alleged “click injection” activities.
Techcrunch later revealed the names of those 3 ad SDK providers: AltaMob, Batmobi and Yeahmobi. Yes, it’s the same Batmobi we are talking about which is also used by sketchy apps.
#Rewarded video will become a more popular ad formats in-app monetization.
— Batmobi (@batmobi) December 7, 2018
Like we can see this ad format monetization grows in hashtag#US and hashtag#EA
Why not try our SDK to monetize by using rewarded video?https://t.co/T2gd01pW59 pic.twitter.com/Z54FJFNRsf
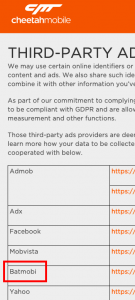
Cheetah Mobile still lists Batmobi in their list of third party data collectors.
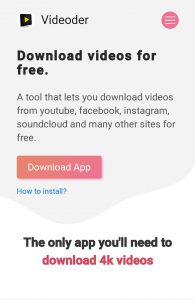
Couple of users posted the issue in Malwarebytes forums. A staff member who goes by the name mbam_mtbr has examined the reports, and confirmed that the Videoder app (package name: com.rahul.videoderbeta) actually uses Batmobi ad SDK.
Several other video downloader apps, like Snaptube (package name: com.snaptube.premium) and TubeMate (package name: devian.tubemate.v3) may also be affected. Google does not allow these apps in Play Store as they violate Google policy on downloading from YouTube.
As a consequence, developers upload their apps on third party sites for sideloading. These sites do not validate underlying SDKs, which makes it easier to include fishy ad providers.
Well well well, what about the Samsung users who did not install any of these apps?
FYI, Samsung actually used Clean Master SDK as part of their Device Maintenance app. They switched to 360 security last year.
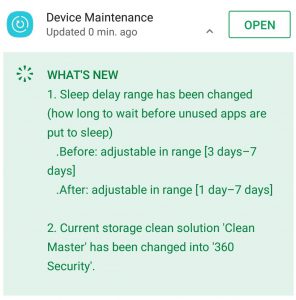
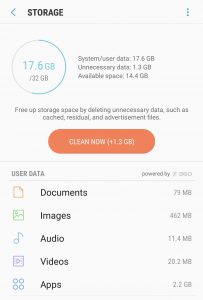
Samsung often bundles app suggestions under this Device Maintenance section on their unlocked models.
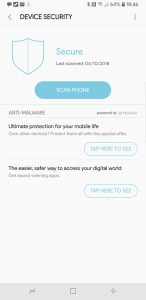
They also send advertisements via their own push service.
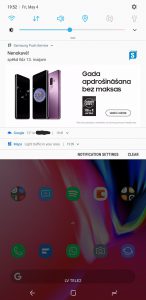
I presume Samsung has ‘accidentally’ included the Batmobi ad SDK in some obscure modules of the Device Maintenance (also called Device Care) app, which is triggering the ads. Remember that the app is now updated through Galaxy Apps and has elevated rights.
As a matter of fact, the original poster of the above mentioned reddit thread has posted the following:
Coincidence? I’m rather sceptical. Another member experienced exact similar issues years ago with a Chinese edition of OnePlus 2 running OxygenOS.
Meanwhile, mbam_mtbr/Nathan has added Android/Adware.BatMobi.xxx in the malware definition which should be included in upcoming database update.
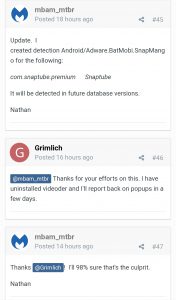
We have contacted Malwarebytes staffs with our findings. The post will be updated accordingly.
PiunikaWeb is a unique initiative that mainly focuses on investigative journalism. This means we do a lot of hard work to come up with news stories that are either ‘exclusive,’ ‘breaking,’ or ‘curated’ in nature. Perhaps that’s the reason our work has been picked by the likes of Forbes, Foxnews, Gizmodo, TechCrunch, Engadget, The Verge, Macrumors, and more. Do take a tour of our website to get a feel of our work. And if you like what we do, stay connected with us on Twitter (@PiunikaWeb) and other social media channels to receive timely updates on stories we publish.


