If you want to import a Mi Mix 3 from China: don't. Wait till it launches internationally.https://t.co/3SoXB6BpsD
— Mishaal Rahman (@MishaalRahman) October 25, 2018
Flashing MIUI Global on Chinese Mix 3 w/ locked bootloader will brick it. If you buy Chinese Mix 3 and don't unlock bootloader, you're stuck with MIUI China.
New updates are being added at the bottom of this story…….
As a hardware maker, Xiaomi has a beefy portfolio of products. Smartphone, tablet, laptop, bluetooth speaker, electric scooter, smartplug, laser projector, rice cooker – you name it!
Xiaomi tried to come up with an Apple-like ecosystem, particularly in Mainland China. Their products, along with in-house software and operating system, are tightly integrated with each other.
They even have alternatives to iCloud & iMessage, namely Mi Cloud and Mi Message. Functionality wise they are at par with their Apple counterparts.
While expanding outside of China, especially India or European countries, Xiaomi faced some hiccups with this setup. People were using and accustomed with other alternative services. To suit their needs, Xiaomi needed to adapt itself with the environment.
In fact, they did. MIUI, their in house skin of Android, was split into two halves: one dedicated for global users and the other one for Chinese people. While the base is same, feature sets vary between two branches.
On the other hand, there are issues with reselling. Third party vendors often resell Xiaomi smartphones in different regions without any authorization. They even install frankenbuild operating systems on Chinese phones to sell them internationally.
Xiaomi introduced a locked bootloader policy since 2016 for extra security. The idea was to prevent unauthorized reselling and minimize the existence of vendor ROMs.
Subsequently anti-rollback protection was launched to make cross-region firmware flashing or downgrading more complicated. PiunikaWeb covered the scenario to some extent in this article.

To comply with the ecosystem, the official bootloader unlock method require a valid Xiaomi account. The account needs to be bound with (i.e. logged in from) the target device for a specific amount of time.
Initially the unlock process involved manual request and verification which was removed later on. Xiaomi provides a Windows-only tool, where user needs to login using their Mi account.
After successful verification, the phone requires to be connected with PC in bootloader/fastboot mode. The tool, named ‘Mi Unlock’, verifies the prerequisites and unlocks the bootloader of the phone.
Xiaomi uses VMProtect to obfuscate their tool from reverse engineers.
VMProtect protects code by executing it on a virtual machine with non-standard architecture that makes it extremely difficult to analyze and crack the software. Besides that, VMProtect generates and verifies serial numbers, limits free upgrades and much more.
Franesco Tescari AKA XDA member franztesca has a knack on Xiaomi’s tools. He carefully observed the working principle of the recovery mode of Mi/Redmi phones and Mi Flash application. At the end of the day, he was able to decode the modifications done by Xiaomi engineers on Google’s SDK platform tools such fastboot and adb.
The result? Xiaomi ADB and XiaoMiTool.
Xiaomi ADB is a modified compiled version of Android Debug Bridge, which allows you to sideload official miui roms to your device via stock recovery.
XiaoMiTool is a Windows tool developed to change rom on Xiaomi devices!
As an extension of the work, he also developed MiUnlockTool – a cross-platform alternative to the bloated ‘Mi Unlock’.
The tool is written on Java, so at least latest version of Java Runtime Environment (JRE) needs to be installed to use it. To use the graphical user interface, JavaFX is also required.
The developer has included easy-to-use scripts for major operating systems like Windows/Linux/macOS to execute the program. Command line parameters should work like the following:
Windows:
MiUnlockTool.bat username password
Linux:
sudo ./MiUnlockTool.sh username password
macOS:
./MiFlashUnlock.command username password
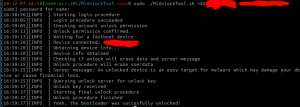
franztesca described the working principle of his work:
original MiFlashUnlock tool is just a bridge between fastboot, you (and your account login credentials) and xiaomi server: the tool gets device info from the device and send them to the server together with the account login token, the server checks wherever you satisfy all their requirements (account authorized, account associated with device in developer settings etc) and if everything is okay the server reply with the unlock key for your device instance (every time you reboot your phone you need a new key).
Then the tool send the key to the device with a custom build of fastboot and if the key is right then the device is unlocked, else it reboots. After I discovered all the process behind the original unlock tool (and all the security encryption techniques) I decided to replicate it with a java (cross-platform) tool which embeds a custom fastboot version and replicates what the original tool does. That’s a simple explaination of how my tool works (obviously it’s more complicated than that).
The tool is still work-in-progress, so novice users are suggested to use the official tool from Xiaomi. For support and queries, make sure to check the support thread and FAQ.
The tool can be downloaded from here. Source code was intentionally made unavailable by the dev.
Update (12 February, 2019)
The developer notified the author via XDA’s Editor-in-Chief Mishaal Rahman about a potential incompatibility.
He noted that the current version of MiUnlockTool is based on v2 of the official Mi Unlock utility. Xiaomi is currently on the v3 branch and new APIs are not yet incorporated inside this project. It may not work at all when Xiaomi drops the support for legacy APIs.
PiunikaWeb is a unique initiative that mainly focuses on investigative journalism. This means we do a lot of hard work to come up with news stories that are either ‘exclusive,’ ‘breaking,’ or ‘curated’ in nature. Perhaps that’s the reason our work has been picked by the likes of Forbes, Foxnews, Gizmodo, TechCrunch, Engadget, The Verge, Macrumors, and more. Do take a tour of our website to get a feel of our work. And if you like what we do, stay connected with us on Twitter (@PiunikaWeb) and other social media channels to receive timely updates on stories we publish.

![[Update: Note from dev] MiUnlockTool unlocks Xiaomi phones' bootloader on macOS and Linux [Update: Note from dev] MiUnlockTool unlocks Xiaomi phones' bootloader on macOS and Linux](https://stage.onepluscorner.com/wp-content/uploads/2019/02/mi_bootloader_unlock_official.png)
