New updates are being added at the bottom of this story…….
Imagine a situation – you are using your phone’s GPS to navigate. Meanwhile a network-level attacker from their secret hideout is doing a man-in-the-middle attack and modifying the position data to guide you to a completely different path!

The aforementioned situation may seem far fetched, but definitely not impossible. Before going into the details, here are some background stories.
It may sound strange, but there are more than one OS running on your phone. Besides the typical Android or iOS you are accustomed with, a number of miniature operating systems exist alongside them.
One of the most prominent example is the cellular modem, which is responsible for handling all the telephony related tasks. The modem runs a tiny independent OS, known as the baseband. It ‘talks’ with Android via the radio interface layer (RIL).
As a matter of fact, hardware components like the GPS, WiFi, Bluetooth or NFC contain such independent firmwares. The main operating system communicates with them via vendor defined interfaces.
In one of our previous articles, we investigated and subsequently uncovered a major glitch in the GPS stack of Xiaomi phones running MIUI. The chinese OEM uses state owned China Telecom server instead of Google’s as SUPL provider for assisted GPS (A-GPS).
Apart from Xiaomi, we took a look inside firmware of other smartphones from different vendors. In fact, we spotted another anomaly in the implementation by a different OEM regarding the AGPS data acquisition (more on that in a bit **).
Chipmaker Qualcomm developed the gpsOneXtra system in 2007, which was later known as IZat XTRA Assistance.
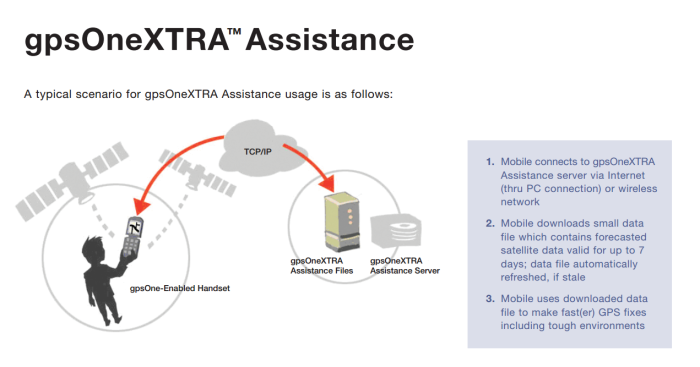
To achieve a faster time to first fix (TTFF), the system enables GPS receivers (for example, your phone) to download the positioning almanac data over the internet from Qualcomm-operated servers.
The data provided by Qualcomm is often being served over plain HTTP, even without a digital signature in some cases. Nightwatch Cybersecurity revealed the vulnerabilities (CVE-2016-5341) in 2016.
Google and Qualcomm promptly addressed and fixed the bugs in December 2016 security bulletin.
A denial of service vulnerability in the Qualcomm GPS component could enable a remote attacker to cause a device hang or reboot. This issue is rated as High due to the possibility of a temporary remote denial of service.
Android internally uses gpsd as a high level software component to get the raw data from the GPS receivers. The usage of gpsd can be controlled via gps.conf, a simple text based configuration file.
In Android environment, gps.conf can be located under /system/etc or /system/vendor/etc or /vendor/etc. However, modern Android versions only allow to place the configurations under the config_gpsParameters section of framework resource.
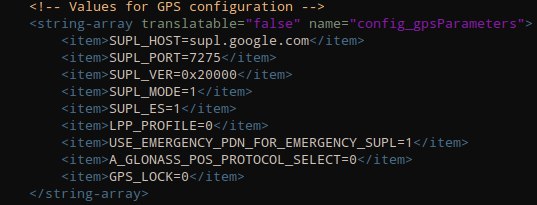
gps.conf can still be used, but only for debugging purpose (gps_debug.conf).
**Let’s rewind back a little – that ‘different OEM’ is none other than OnePlus! Their engineers overrode standard AOSP policies and shipped debug build of gps.conf in OxygenOS.
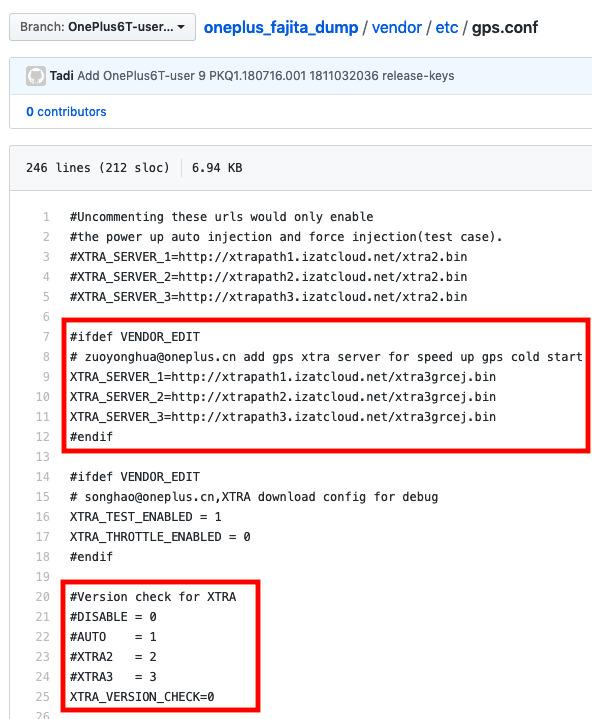
The first highlighted area shows that a Chinese OnePlus engineer has forcibly (VENDOR_EDIT) enabled insecure XTRA data servers.
The second area is more interesting as they do not want to check the XTRA data version. The significance of the version number is as follows:
- xtra.bin – XTRA 1.0 files, providing GPS assistance data (protected by a CRC checksum)
- xtra2.bin – XTRA 2.0 files, providing GPS and GLO assistance data (protected by a CRC checksum)
- xtra3grc.bin – XTRA 3.0 files, providing GPS, GLO, and BDS assistance data (protected by a digital signature). These files have been available since 2014.
With the help of LineageOS contributor Louis Popi aka h2o64, we verified that these changes would force the phones to download the almanac data via insecure HTTP channels.

The 6th, 8th and 11th row of the table shown in the above image indicated that the requests were made and granted over HTTP servers. It was a snapshot of /data/vendor/location/xtra/xtra.sqlite.
We filed a bug report in the feedback section of the OnePlus forum in February, but did not get any response initially.
Later on, with the help of OnePlus community moderator Funk Wizard, the issue got escalated. Yesterday, Jeff H. from OnePlus Bug Hunter team contacted us and ensured that the issue will be fixed “in the upcoming updates”.
They claimed the following:
For the downloading under XTRA, the device is reading the address in Modem NV config, which is going through HTTPS instead of HTTP, and GPS.conf has been already ignored, so the XTRA config won’t be working. Thanks for the feedback anyways, and we will Synchronize the GPS.conf to HTTPS in the upcoming updates to fix the issue.
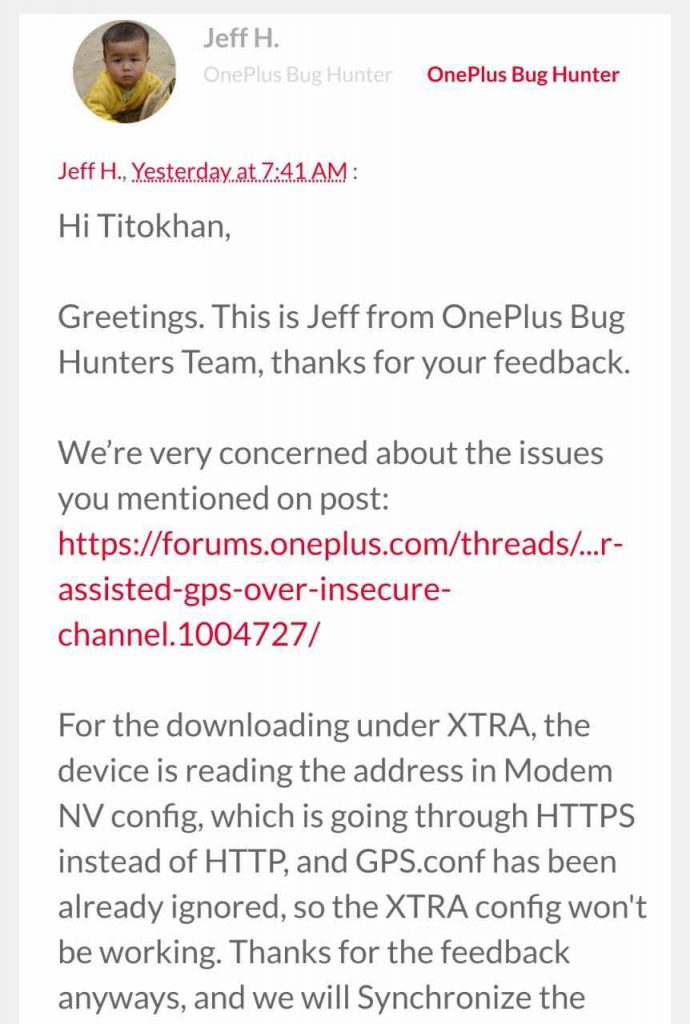
The response from OnePlus Bug Hunter suggests the erroneous code we pointed out isn’t executing currently, but our findings reveal otherwise.
We have shared further test results with them to show the overriding in action. They have yet to respond. We will update the story when we get more information from them.
The presence of hardcoded HTTP URLs is itself a prime example of malpractice. Moreover, OnePlus will switch them to HTTPS “anyway”, which validates the weight of our claim.
Interesting fact, this ‘VENDOR_EDIT’ approach can be spotted in multiple occasions inside source codes published by OPPO. Given the close relationship between OnePlus and OPPO, I’m not surprised. ?
Besides Louis, I like to thank developers like phhusson, luk1337 and jrizzoli for assisting me and validating this proposition.
Update (April 17)
OnePlus silently patched the security vulnerability related to GPS XTRA data downloading in latest Open Beta release. The current gps.conf looks like the following:
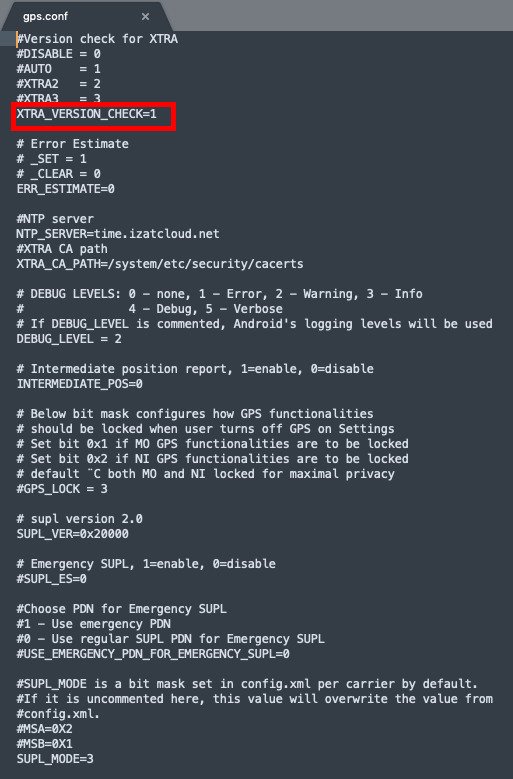
For more details, see here.
PiunikaWeb is a unique initiative that mainly focuses on investigative journalism. This means we do a lot of hard work to come up with news stories that are either ‘exclusive,’ ‘breaking,’ or ‘curated’ in nature. Perhaps that’s the reason our work has been picked by the likes of Forbes, Foxnews, Gizmodo, TechCrunch, Engadget, The Verge, Macrumors, and more. Do take a tour of our website to get a feel of our work. And if you like what we do, stay connected with us on Twitter (@PiunikaWeb) and other social media channels to receive timely updates on stories we publish.

![[Patched] EXCLUSIVE: Your OnePlus phone may be downloading some GPS data over insecure channels [Patched] EXCLUSIVE: Your OnePlus phone may be downloading some GPS data over insecure channels](https://stage.onepluscorner.com/wp-content/uploads/2019/02/gps_pokemon_go.jpeg)
