Ever since mobile phone had become a daily driver, it has been helping the authorities to solve crimes. Following the data from the gadget (be it the location, call logs, or SMS), deciphering mysterious felonies turned out to be easier than it was in the past.
The forensic experts have to go through multiple complicated processes to extract information from a mobile phone. Owing to the hardships for surpassing the modern day encryption methods, it might take long to mine details from a locked unit.
Let’s leave the generality and take a specific device into consideration, iPhone! One of the reason why Apple keeps the iOS system so closed is that it slims the chances of attracting cyber attacks. And, they have succeeded in the attempt to a great extent as well.
What if a forensic expert gets a locked iPhone from a crime scene? Yeah, details should be drawn out from the device to throw light on the misdeed. But with the Cupertino company patching up the vulnerabilities with each firmware overhaul, intruding into the OS is a bit far-fetched.
Wait what! Elcomsoft, a mobile forensic tools developing company has found a way to do exactly the same. First in the process, they got the iPhone jailbroken. How did they do that on a locked handset, you may ask! Well, it’s possible using checkra1n.

In case you are naive, checkra1n uses checkm8 exploit, which deals with a bootrom vulnerability. And, by using it, you can jailbreak an iPhone right from the DFU mode. The method is evergreen because Apple can’t fix the flaw through OTA updates.
Once they jailbroke the test unit with checkra1n, then they ran their iOS Forensic Toolkit, gave 44 as the port number, and entered ‘alpine’ as root password. When the screen lock is unknown, the tool can only output a limited set of information.
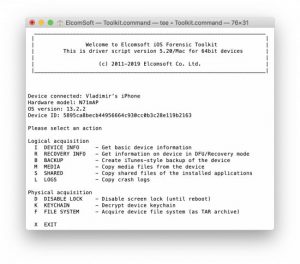
In order to get the complete filesystem and the keychain, you will have to unlock the device. Keychain, as it contains the credentials and encryption keys for different services, can’t be decoded with the system lock on.
Are you wondering what type of files come up before unlocking? The most critical ones won’t surface. Still, one can sneak into a number of files that would reveal the identity of the phone’s owner. The details include
Logs, preferences, profiles
/private/var/installd/Library/Logs/MobileInstallation/
/private/var/log/
/private/var/preferences/
/private/var/root/Library/Preferences/
/private/var/mobile/Library/Logs/
/private/var/mobile/Library/Preferences/
/private/var/mobile/Library/UserConfigurationProfiles/
System databases
/private/var/wireless/Library/Databases/CellularUsage.db
/private/var/wireless/Library/Databases/DataUsage.db
/private/var/root/Library/Caches/locationd/consolidated.db
/private/var/mobile/Media/Downloads/downloads.28.sqlitedb
/private/var/mobile/Library/ApplePushService/aps.db
/private/var/mobile/Library/FrontBoard/applicationState.db
/private/var/mobile/Library/TCC/TCC.db
Call log and iMessage/SMS (temporary databases)
/private/var/mobile/Library/CallHistoryDB/CallHistoryTemp.storedata
/private/var/mobile/Library/SMS/sms-temp.db
Voice mail
/private/var/mobile/Library/Voicemail/voicemail.db
List of accounts
/private/var/mobile/Library/Accounts/Accounts3.sqlite
(Source)
Of course, this marks a remarkable step in the forensic department. Speaking of the toolkit, it isn’t available for free of cost. One needs to spend $1,495 (local pricing may vary) to bag the latest edition.
Note:- Stay tuned to our iOS section for similar stories.
PiunikaWeb started as purely an investigative tech journalism website with main focus on ‘breaking’ or ‘exclusive’ news. In no time, our stories got picked up by the likes of Forbes, Foxnews, Gizmodo, TechCrunch, Engadget, The Verge, Macrumors, and many others. Want to know more about us? Head here.


