Remember when Microsoft pushed the free Windows 10 update to users having older version of Windows (7, 8 and 8.1)? Many early adopters, who accepted the offer, eventually wanted to restore the previous instance due to multiple reasons.
Well, that was kind of difficult for them.
This article is not about the reasons to ditch Windows 10, rather we are trying to concentrate on the possible issue(s) with downgrading. In case of major operating systems, most of them offer a direct upgrade path to the latest version.
However, the reverse, i.e. a seamless downgrade option is almost non-existent – be it Windows or Linux or macOS.
The same practice can be seen in case of low level firmware updates or embedded OS patches as well. The internal structure of the new builds are often drastically different from the initial builds, thus offering a safe and secure downgrade option is not feasible.
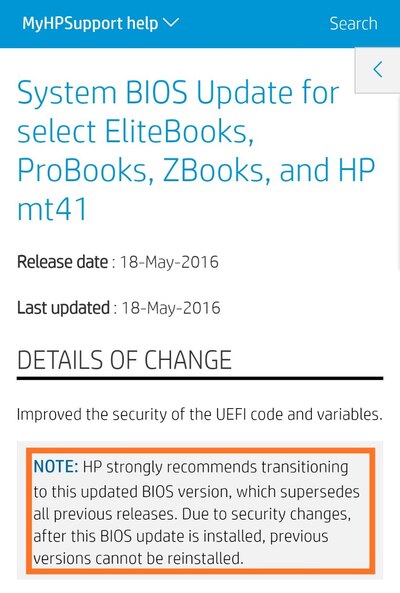
In past, Android manufacturers implemented their own variations of rollback protection mechanism. With the release of Android 8.0 Oreo, Google introduced a standardised format of downgrade prevention dubbed as Anti-rollback Protection (ARB), which was part of Android Verified Boot 2.0.
AVB includes Rollback Protection which is used to protect against known security flaws. Each VBMeta struct has a rollback index baked into it like the following:
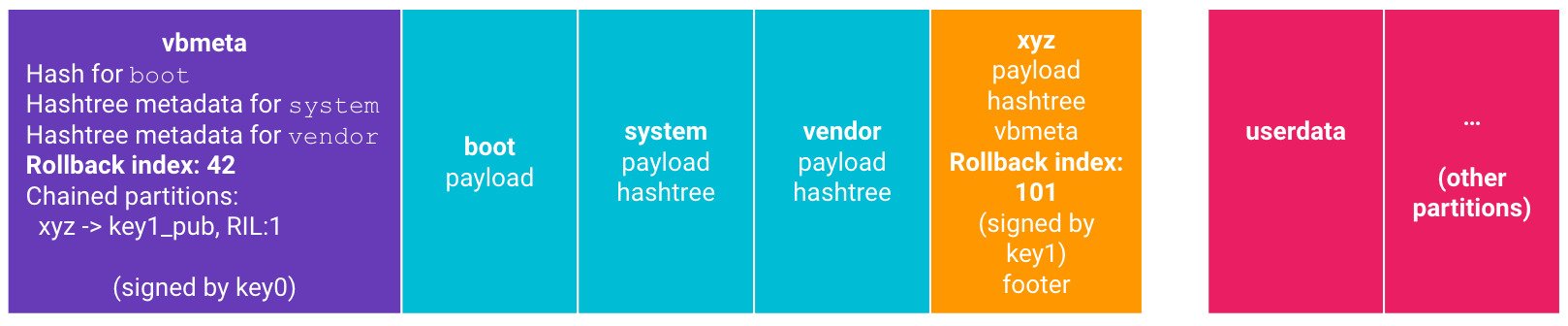
Xiaomi included the aforementioned rollback protection in MIUI with the release of 2018’s Redmi Note 5 (China) / Redmi Note 5 Pro (India). However, their weird implementation forced to brick multiple phones as ARB triggered – even when the was bootloader unlocked.

Since then, the Chinese OEM continued to include the rollback protection on multiple Xiaomi and Redmi branded phones. The choice seems random, as the Redmi Note 6 Pro (codename:tulip), aka the successor of Redmi Note 5 Pro (codename: whyred), didn’t feature ARB.
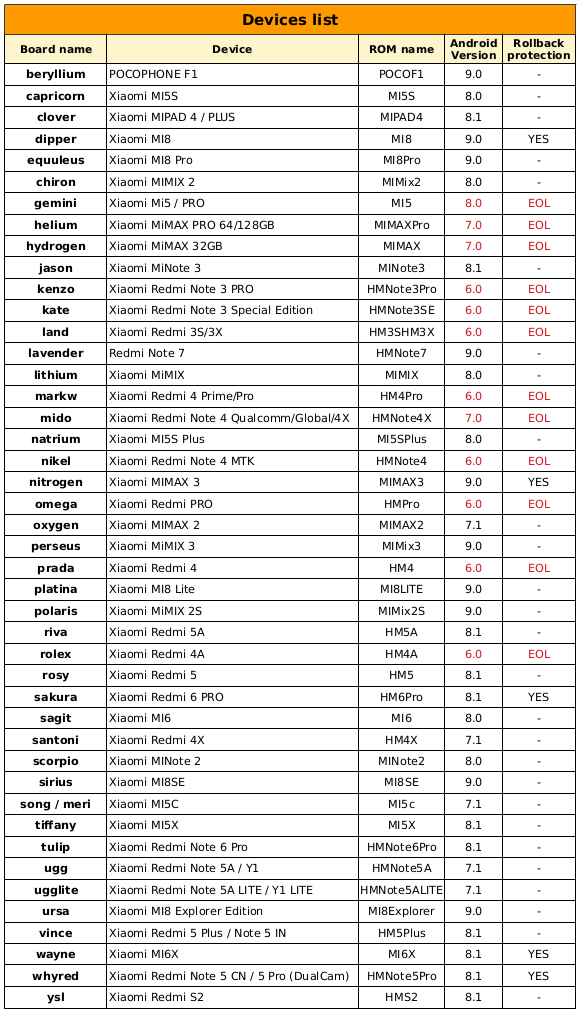
Thought it can be possible to view the current rollback index number on a Xiaomi phone running MIUI by querying the value via fastboot, it is not convenient for regular users.
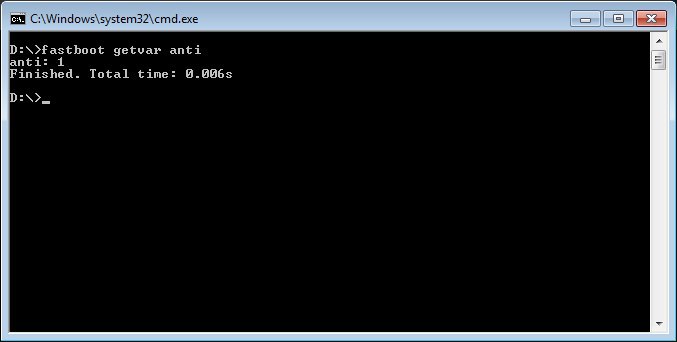
The significance of the values of the ‘anti’/ARB parameter is as follows:
- 1: Anti-rollback protection is disabled.
- 3: Anti-rollback protection is enabled and can be enforced.
- 4: Anti-rollback protection is enabled, has already been increased from previous value (3).
- 5 (or higher): We have not seen it, but technically it can exist.
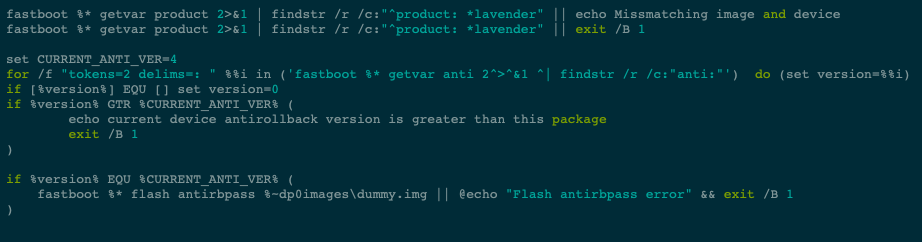
It can be possible to get some info of the ARB index value by examining the MIUI fastboot flashable package from Xiaomi for a particular device. The flashing script should show the following snippet:
The community found a way to extract the value of the firmware package (xbl.elf aka eXtensible BootLoader to be precise) itself. One can use a hex editor to look for the ‘Californial’ string inside the xbl.elf binary.
– go to line 0x1480
– you will see something like “0.00000X000” and above it will be “californial”
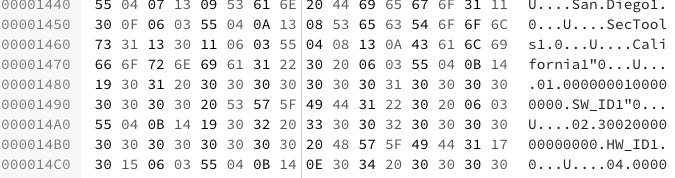
– if X is 1, that means that this rom doesnt have antirollback meaning that if you dont have arb, you can downgrade to that version or install it without getting the ARB, but if you have ARB you cant install it or you will brick your device.
– if X is 4, that means that this rom has antirollback meaning that if you dont have arb, you will get it when you install this rom, and for ARB users as long as this is a higher version than the one you have currently installed on your device you can install it safely without bricking your device
This method is suitable for both MIUI recovery and fastboot packages as the firmware files can easily be extracted from them.
Based on the above concepts, eminent developer yshalsager (founder and maintainer of Xiaomi Firmware Updater project) has created a handy Python script to check the ARB index value of MIUI fastboot and recovery update packages without installing any extra tool.
Python 3 is included in most common Linux distributions. Windows and macOS users can grab the latest installer directly from the official website and install it.
Afterwards, users should download the open source script from GitHub using git clone or direct download method and execute like the following:
python3 miui_arb_checker.py MIUI_FIRMWARE_FILE_NAME
For example, we’ve tested it on the closed beta build of Android Pie for Mi MIX 2. The output is as follows:
python3 arb.py miui_MIMIX2Global_9.5.8_abbfb1e4ff_9.0.zip ARB index is: 1

Thanks to the open source nature of the script, one can easily improve and/or add support for future changes from Xiaomi by appropriate contributions. For end users, there should be less fear of accidental bricking due to wrong flash.
Having a Xiaomi/Redmi/Poco phone? What is the current value of its anti-rollback index?
PiunikaWeb is a unique initiative that mainly focuses on investigative journalism. This means we do a lot of hard work to come up with news stories that are either ‘exclusive,’ ‘breaking,’ or ‘curated’ in nature. Perhaps that’s the reason our work has been picked by the likes of Forbes, Foxnews, Gizmodo, TechCrunch, Engadget, The Verge, Macrumors, and more. Do take a tour of our website to get a feel of our work. And if you like what we do, stay connected with us on Twitter (@PiunikaWeb) and other social media channels to receive timely updates on stories we publish.


