Exploiting Qualcomm EDL Programmers: Memory & Storage based attacks allowing PBL extraction, rooting, secure boot bypassing & bootloader chain debugging/tracing. Multiple Qualcomm based mobile devices affected (5-part blog post)https://t.co/b235CAaCSh
— Aleph Research (@alephsecurity) January 22, 2018
Qualcomm is a major silicon vendor for Android smartphones. The flagships from major OEMs like Samsung, Google, OnePlus or Xiaomi are mostly based on Qualcomm based SoCs.
For their massive presence in Android ecosystem and open source code contributions to Code Aurora Forums (CAF), Qualcomm becomes synonymous with aftermarket developments. As a consequence of such tinkerings, many phones are getting bricked. The internet is full of these ‘unbricking’ guides for Qualcomm SoC based devices.
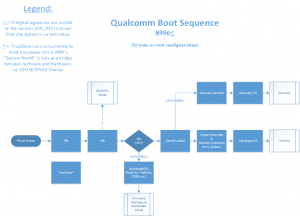
Qualcomm based devices come with Emergency Download Mode (EDL), a special boot-mode of the Qualcomm Boot ROM (Primary Bootloader/PBL). To use this mode, users need to access OEM-signed programmers that are often leaked across forums and other platforms. Some OEMs like Xiaomi officially publish them as part of firmware packages.
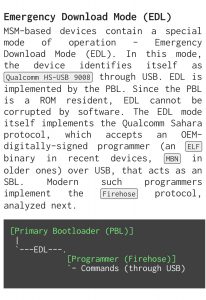
Security researchers from Aleph Research disclosed multiple security vulnerabilities around Qualcomm EDL mode and associated exploits in OnePlus phones (see here, here & here) in past. Readers may notice that OnePlus related forums were mentioned frequently (example: here, here, here) while discussing about the leaked programmers.
Exploit Targets Qualcomm's EDL Mode, Affects Some Xiaomi, OnePlus, Nokia and other Devices https://t.co/gdg1aGpcq6 pic.twitter.com/JSSmFXrjNg
— XDA (@xdadevelopers) February 10, 2018
The reason is quite simple: OnePlus hasn’t patched the vulnerability to boot to EDL mode directly using key-combo till date.
OnePlus technicians often offer remote assistance for resolving issues. They download the programmers and firmware files to end users’ PC in encrypted form, decrypt them, flash the phone and deletes them before ending the session. For tech-savvy users, sniffing the decrypted package in between is a cakewalk.
In some case, the second level technicians share the URLs of the encrypted packages with the customer beforehand. FYI, a single unbrick package for typical OnePlus phones sizes about 1.5 GB. The customer downloads the package and inform the technician to perform the flashing.
With a large scale community effort, several vulnerabilities can be located inside this chain of trust and OnePlus security policies. After gathering a lot of direct links of such packages, finding the pattern and reconstructing the URL tree are trivial.
It can even be possible to traverse through the servers where OnePlus is storing these unbrick packages. OnePlus doesn’t employ an extra layer of authentication there, thus downloading them is not at all difficult.
And it feels the same for decryption as users from popular Android modding forums are dumping and mirroring them for convenient usage (example: here, here).
For power users, the aforementioned packages are handy to unbrick and completely restore their devices to factory state. Downgrading to a previous version of Android (e.g. from Pie to Oreo) is also possible using these files. One can easily convert their Chinese OnePlus phones to global version (or vice-versa) with the same packages.
On the other hand, a rogue user can also use them to bypass factory reset protection (FRP). With proper knowledge and toolset, someone can easily dump device contents or unlock the bootloader without wiping the internal storage.
Some of the packages are available on OnePlus’ own official forums (example: here, here). Moderators even made them sticky, thus the affairs are quite public in nature.
Perhaps the most practical example of (ab)using the situation is to convert T-Mobile OnePlus 6T to unlocked international variant (here is why people may want to do so).
“Words kill, words give life”.
PiunikaWeb is a unique initiative that mainly focuses on investigative journalism. This means we do a lot of hard work to come up with news stories that are either ‘exclusive,’ ‘breaking,’ or ‘curated’ in nature. Perhaps that’s the reason our work has been picked by the likes of Forbes, Foxnews, Gizmodo, TechCrunch, Engadget, The Verge, Macrumors, and more. Do take a tour of our website to get a feel of our work. And if you like what we do, stay connected with us on Twitter (@PiunikaWeb) and other social media channels to receive timely updates on stories we publish.


