The mainrepo malware ("MobileSafeMode.dylib") sends your UUID to a server, the server then has the ability to send back any command that should be executed on your device. It's essentially a backdoor that's running inside SpringBoard and Cydia. pic.twitter.com/QcY4rFnRDg
— opa334 (@opa334dev) March 23, 2021
So we all know about jailbreaking, the iOS equivalent of rooting on Android. This allows users access to restricted parts of iOS, thereby enabling various system-level changes and tweaks.
Needless to say, many OEMs frown upon rooting and the same goes for jailbreaking as this is one of the sure ways to lose your warranty.

But why is that? Well, such system-level tweaks come with a certain level of risk, be it from tweaking the wrong thing and bricking your device, or from using modules that haven’t been properly vetted.
A few weeks ago, there was a scandal surrounding one of tweakers’ most popular jailbreak repository on the interwebs, MainRepo.
This, after it came to light that the popular repository has been sneakily injecting malware onto jailbroken devices.
According to one popular tweak developer, Opa334, MainRepo shared infected devices’ serial number, Mac address, and ECID with its servers, allowing them to run any commands on the said devices.
The mainrepo malware (“MobileSafeMode.dylib”) sends your UUID to a server, the server then has the ability to send back any command that should be executed on your device. It’s essentially a backdoor that’s running inside SpringBoard and Cydia.
The damning revelations further went to confirm that MainRepo went to sneakily hide the malware contained in their product by renaming them to less suspicious names while they remain the same.
– MobileSafeMode.dylib
– RocketBootstrapUI.dylib
– SnowBoardSB.dylib
– MainRepoEGG.dylib
(Source)
These damning reports were later on corroborated by ESET Research, giving a more detailed account of the inner workings of MainRepo’s malware.
This was unsettling news for the jailbreak community as one of the greatest fears of the whole jailbreak idea had come true, a big player taking advantage of its users.
Well, until now. In what could be seen as a major win for advocates of user privacy and ethical jailbreaking, MainRepo’s domain has been suspended.
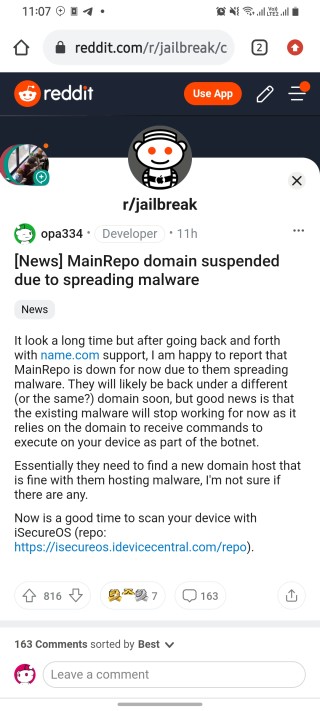
It took a long time but after going back and forth with name.com support, I am happy to report that MainRepo is down for now due to them spreading malware. They will likely be back under a different (or the same?) domain soon, but good news is that the existing malware will stop working for now as it relies on the domain to receive commands to execute on your device as part of the botnet.
Essentially they need to find a new domain host that is fine with them hosting malware, I’m not sure if there are any. Now is a good time to scan your device with iSecureOS.
In a message posted on Reddit by the same whistleblower developer, the news of MainRepo domain being suspended was announced and in it, the clarification that infected devices now don’t have a base to report back to.
This only goes to reiterate the common rhetoric about the inherent risks associated with any such venture and thanks to whistleblowers like Opa334, our devices are a tad bit safer..for now.
Someone, please give this man a beer!
NOTE: We have these and many more jailbreak stories in our dedicated iOS section so stay tuned.
PiunikaWeb started as purely an investigative tech journalism website with main focus on ‘breaking’ or ‘exclusive’ news. In no time, our stories got picked up by the likes of Forbes, Foxnews, Gizmodo, TechCrunch, Engadget, The Verge, Macrumors, and many others. Want to know more about us? Head here.